Olympic threats designed to trick you
Are you planning to visit Brazil during the Olympic Games? Or watch it online? In this blog post we discuss the threats to visitors aiming to travel to Brazil to watch the games and to those planning to watch it online. In the first part we’ll talk about phishing attacks, including one against the organizers of the Games; in the second we highlight WiFi security and the results of the wardriving we did on the streets of Rio, visiting the same places as tourists and the athletes. In the third and final part we touch upon physical security that involves the usage of USB charging spots at airports, the problem of credit card cloning and ATM skimmers that will directly affect visitors to this summer’s Olympic Games in Rio.
It is clear that using the Olympic Games theme is very attractive to the bad guys. Cybercriminals always use popular sports events as bait for their attacks, as they did it in the 2014 World Cup - an event we monitored very closely due to the impressive amount of attacks registered at the time, mainly in Brazil. But the forthcoming Olympic Games has been a bit different. The number of attacks has been low, compared with the World Cup. There are many reasons to explain it one of which is that the International Olympic Committee (IOC) keeps a very active Security Operations Center (SOC), working and treating the security incidents, reporting phishing and malware campaigns. As a result, the number of “in-the-wild” attacks targeting users at this time are low.
However, the bad guys have no limit when it comes to creating new attacks. We were able to track and block several of them, such as the registration of malicious domains, fake giveaways promoted on social networks and, of course, websites selling fake tickets, using all possible ways to trick users.
The rise of bad domains
Most of the attacks start with the registration of a domain that clearly shows its malicious intent. Since the beginning of the year, we monitored the creation of new domains registered with the name of the city that will held the games. In fact, we found that the bad guys are constantly registering new creations at the start of every attack. Our blacklist contains more than 230 of these bad domains.
Several of these domains were registered via a free webmail account or use domains as protection to hide the real identity of the owner. Some of these domains are hibernating, waiting for the right moment to start an attack (especially those promising free streaming). Others were used to host fake ecommerce sites selling tickets, hosting phishing, malware, or even used to spread fake ticket giveaways. Another interesting point is that several of these domains are already using the new gTLD approved by ICANN (such as .tech and others).
The phishing phenomenon
It’s not only end-users who are targets of phishing attacks. Brazil tops the list as the most attacked country with this type of scam, and employees of the Games organization were also targeted for their potentially lucrative credentials. In February we identified a very interesting targeted campaign, on our domain monitoring system, against the IOC using the malicious domain masquerade as their Intranet portal. The purpose of the attackers was to steal credentials of IOC employees working in Brazil. The fake site looked like this when it was live and we are also aware of several other attacks including this one:
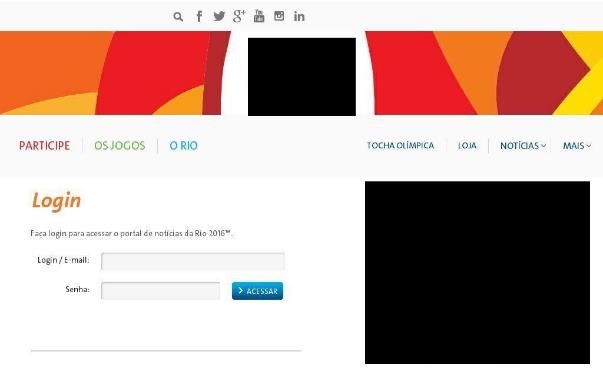
IOC employees were the target of phishing campaigns to steal credentials
The most common attacks are those that aim to phish the final user - stealing credentials is a very easy attack that even a non-skilled criminal can do. We saw phishing scams with different goals, in several colors and guises. This one was very popular in Brazil and aims to clone your credit card using the name of a Brazilian company and promising to giveaway a new car and tickets to the Games:
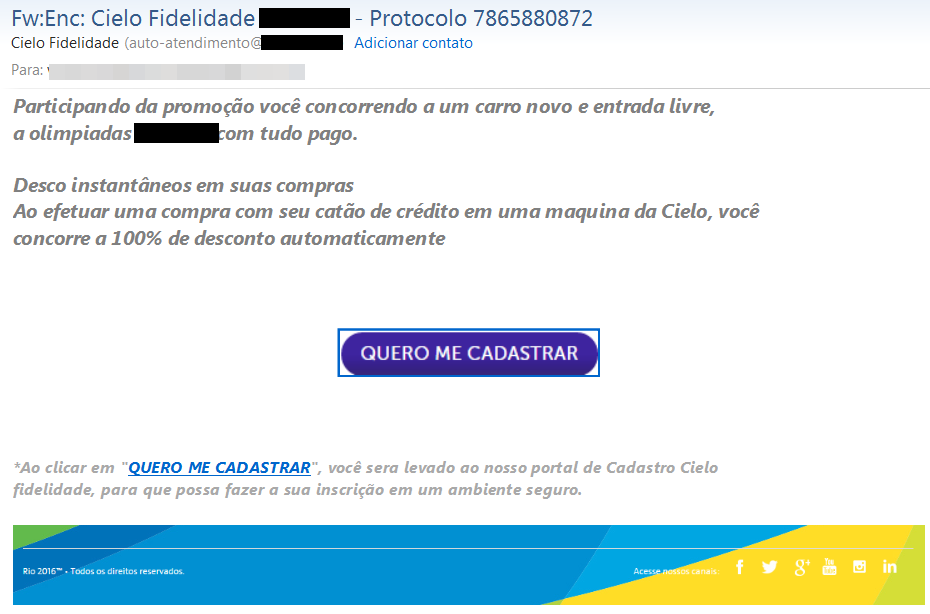
Free tickets and car giveaway. All fake promises.
Fake tickets, fake giveaways, real losses
As happened during the last World Cup, most of the malicious e-mails sent by the Brazilian bad guys used free tickets to watch the Games in Rio as the bait. Some of these messages also pointed to fake websites. This is a good example of a very well done campaign, promising the direct sales of tickets without applications to the official lotteries, that take place for people living in Brazil:
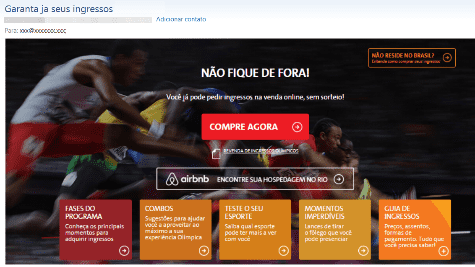
Why bother to participate in the official lottery when you can buy a ticket direct from a fraudster?
Other fake websites also offered tickets with a very low price, to attract people looking to buy tickets at the last hour. This website, targeting Brazilians, looks good but on closer inspection it is written in poor Portuguese:
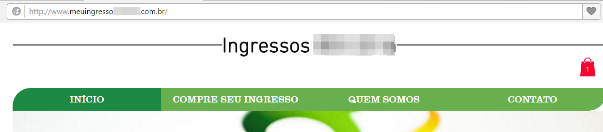
The purpose here was to sell fake tickets with the victim paying but receiving nothing. The payment method selected by the fraudster was Brazilian boletos, a very popular payment system, used mostly for people that don’t have credit cards.
The bait to attract the attention was very low prices. The ticket to the inaugural ceremony cost U$500.00 and a match of the Brazilian National Football Team cost only U$ 50.00. Of course everything was fake:
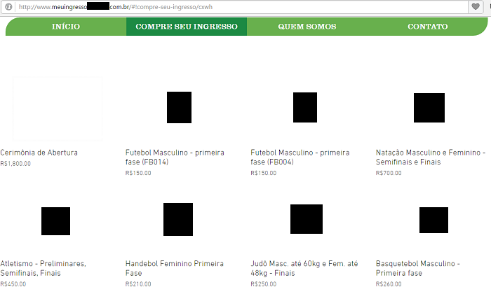
“Watch the Male Football match paying only U$ 50,00”
Bad guys also used social media to spread their attacks. Facebook was the most used network in these cases, such as this fraudulent page announcing a fake ticket giveaway. The page is still online:
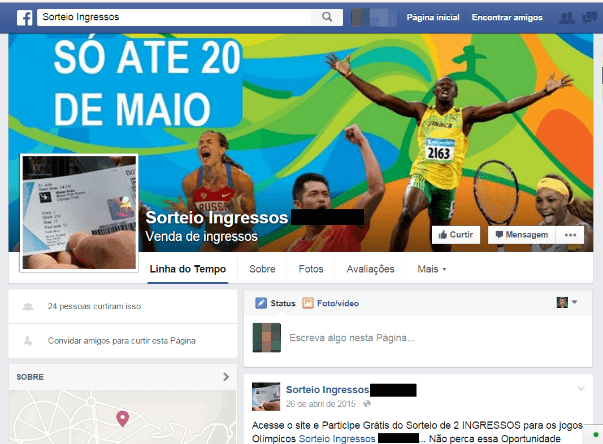
If you want to watch the games, it’s too late to buy tickets via the official channels. We do not recommend buying through unofficial markets as there is a high possibility that you are buying a pig in a poke. To make sure you don’t get caught out, the best thing is to watch the games on TV or online - but be aware of malicious streaming websites, as they will undoubtedly appear in a last ditch attempt by the bad guys to try and infect your computer and steal your data.
WiFi security
When we travel, we usually access the Internet more to help stay in touch, tweet, post status updates and share pictures. However, international data plans are usually very expensive and this is why we look for WiFi hotspots. Cybercriminals know this and every year set up fake access points or compromise legitimate WiFi networks to intercept and manipulate their victim’s browsing. Their focus for the attack is user’s passwords, credit cards and other sensitive personal information. Open and misconfigured WiFi networks are actually preferred vehicles for criminals.
To identify the extent of the problem in Brazil, we drove by three major areas of the Olympic games and passively monitored the available networks which visitors are most likely to try and use during their stay – the Brazilian Olympic Committee building, Olympic Park and the stadiums (Maracanã, Maracanãzinho and Engenhão).
Beautiful beaches, bossa nova and insecure WiFi
Running a fast recognition over two days and on the map marked with a star sign, we were able to find about 4,500 unique access points located in the aforementioned areas.
Most of the networks actually work on the 802.11n standard:
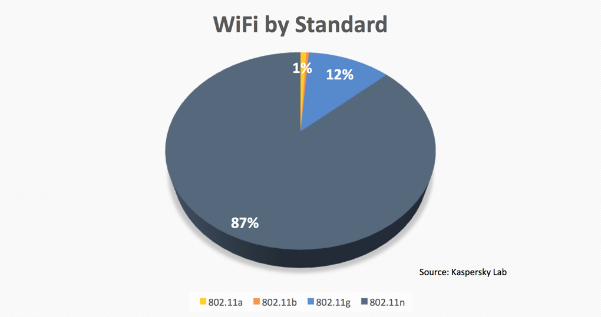
That means that most of the hardware used to build the WiFi access points is new and works especially well for multimedia streaming, reaching speeds of up to 600Mbps and working not just on 2.4Ghz and 2.5Ghz but also 5Ghz.
However, when it comes to their security, 18% of all available WiFi networks in the area are insecure and openly configured. That means that all data sent and received in such networks is not protected by any encryption access key.

We can see that additionally 7% of all networks are WPA-personal protected. That algorithm is actually obsolete today and can be broken with minimal effort. In our opinion this is especially concerning as users who connect to their “trusted” networks may believe that they are actually connecting to a secure network, when in reality it could be compromised by an attacker, who could deliver different kind of attacks to manipulate network traffic with user’s data.
So, about a quarter of all WiFi networks in the areas of the Olympic games are insecure or configured with weak encryption protocols. This means that the attackers can break them first and then develop technical circumstances to sniff victim’s navigation data and steal their sensitive data.
Is it possible to use an open WiFi network and still have a secure Internet connection? The answer is yes, however only when using a VPN connection.
We strongly recommend, regardless of any WiFi network you use while travelling, to use a VPN connection, so the data from your end-point travels to the Internet through an encrypted data channel. This way even if you work from a compromised WiFi network, the attacker might not get access to your data.
However not all VPN providers actually offer the same good service. Some of them are vulnerable to DNS leak attacks. That means that even if your immediate sensitive data is sent via VPN, your DNS queries or requests are sent in plain text to the DNS servers set by the access point hardware. In this scenario the attacker can still at least know what servers you are browsing and then, if it has access to the access point of the compromised WiFi network, can define malicious DNS servers. That would essentially mean, next time you type the name of your bank in the browser, the IP address where it goes to will be a malicious one. So, even some experienced users may become an easy victim for the attackers. There is almost no limit from the attackers’ point of view when they have control of your DNS servers.
So, before you use your VPN connection, make sure it does not have a DNS leak problem. If your VPN provider doesn’t support its own DNS servers, you might consider another VPN provider or a DNSCrypt service, so your DNS requests will make external and encrypted queries to secure DNS servers. Remember that what starts as a small security issue could have big security implications.
A simple formula must be this: any network you connect to, use your VPN connection with its own DNS servers. Don’t rely on any local settings since you can’t be sure if the WiFi access point you connect to is compromised or not.
Physical security
Another point that requires vigilance when travelling is physical security - not everything that is useful is exactly what it seems. Criminals often use tactics to deliver malicious attacks on situations where you do not necessarily think there is a risk. Let's look at some common situations where this could happen.
USB charging spot

As mentioned before, using a mobile phone when traveling is crucial and it can be a big challenge to keep it sufficiently charged all day long. In order to help tourists, most cities are investing in charging points that can be easily found in shopping malls, airport and taxis. Most of them provide connectors for the majority of phone models as well as a USB connector that can be used with your own cable.

Charging spot provided in a Brazilian cab
Some models usually found in shopping malls and airports also provide a traditional power supply that can be used with your own charger.

Charging spot at Rio International Airport. Which one do you think is the most secure?
While connected via USB, the attacker can execute commands in order get information about the device including the model, IMEI, phone number and battery status. With that information it is possible to run an attack for the specific phone model and then successfully infect the device and collect personal information.
This doesn’t mean that we should never charge our devices when away from home, but by following these simple rules you can protect yourself from this kind of attack:
- Always use your own charger and avoid buying one from unknown sources;
- Use the power outlet instead of USB socket when using an unknown charging point;
- Don't use the charging cables at a public charging spot.
ATM skimmer
The ATM skimmer attack, also known as "Chupa-cabra" in Brazil and other countries in Latin America, is a very popular type of attack that is still being used by criminals in Brazil. From time to time a new gang appears on the news delivering this attack somewhere across the country, mainly in places commonly frequented by tourists, such as the Rio International Airport. In 2014 a gang installed 14 ATM skimmers there.
There are different types of ATM skimmers in Brazil, the most common just installs a reader for the card and a camera in order to record the password as it is typed.

An ATM skimmer which installs a camera to record the typed password
For this type of skimmer you can protect yourself by hiding the keypad while typing the password which will avoid your password from being recorded by the installed camera.
Unfortunately, this method will not help in all cases, as there is another type of skimmer where criminals replace the entire ATM, including the keypad and screen. In this case, the typed password will be stored on the fake ATM system.

ATM Skimmer which replaces the entire ATM
In order to avoid this type of attack it is important to be aware of any suspicious behavior while using the ATM.
- Check if the green light on the card reader is on. Usually they replace the reader with a version where there is no light or it is off.
- Before starting the transaction, check if there is anything suspicious on the ATM such as missing or badly fixed parts;
- Hide the keypad while typing your password.
Credit Card Cloning
Unfortunately, Brazil is well known for its credit card cloning activities and it is not hard to find someone who had their card cloned while visiting the country.
Credit and debit cards are widely used in Brazil and almost everywhere accepts cards as payment methods - including street vendors. Actually most of them prefer credit card payments in order to avoid problems with the change.
Brazilian banks are referenced across the world regarding their fight against credit card cloning as well as their pioneer status in adopting chip-based cards to protect customers from this type of attack by making it much harder to clone the card. However, it was only a matter of time before Brazilian criminals would find a way to start cloning the chip-based cards, by exploiting flaws in the EMV transaction implementation.
We could see Brazilian criminals exchanging information about how to execute an attack on a chip-based card in order to extract the information and then write it back to another card using some tools.
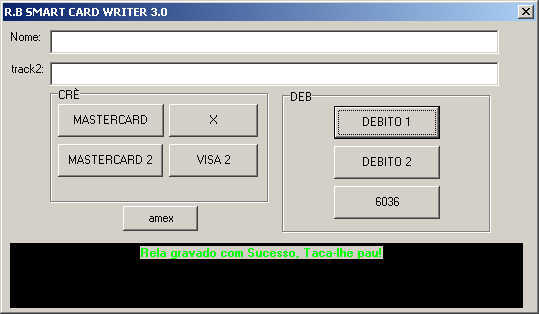
Tool used to save the information to the smart card
It is really hard to protect yourself against this type of attack, because usually the point-of-sale is modified in order to save the information, to be collected later by the criminals. Sometimes they don't need physical access to extract the stolen information as it is collected via bluetooth.
One good solution from the banks is SMS notifications for each transaction made using your card. Even though it does not avoid card cloning, the victim will be notified about the fraudulent transaction as soon as it happens then it can contact the bank in order to block future transactions.
To reduce the chances of having your card cloned, there are some simple steps to take:
- Never give your card to the retailer. If for some reason they cannot bring the machine to you, you must go to the machine;
- If the machine looks suspicious, change the payment method. It is always good to have some money with you as a back-up;
- Before typing your PIN make sure you are on the correct payment screen and that your PIN is not going to be shown on the screen.
For everybody visiting Brazil to watch the games, we wish you safe flights and a safe stay. To our readers we wish you safe online surfing and for the Olympic athletes, may the best one win!
